TAG Explainer for Solid
This document was created using the TAG template for explainers
User-facing problem
Users spend most of their time online on platforms like social networks, email, banks, e-commerce platforms, etc. The personal data which represents their action and interaction on each platform is stored by the company-specific back-end servers on chase.com, facebook.com etc. Because of the lack of interoperability between those platforms, users are disempowered. They cannot for example easily
- Share financial data with an accountant and a set of family members
- Allow their medical data to be used for research in a clinical trial
- Share Facebook photos with LinkedIn colleagues
To achieve these things they must choose between moving all of their activity to one platform, or painfully copying medical data, photos and groups between platforms. As users of the Web, we require standardized identity and standardized personal data storage, such that our data can flow responsibly across different systems between which people can choose.
There are other challenges which Solid helps to address, but we will focus on this area for this explainer.
Developer-facing problem
When a developer writes apps that involve personal data, things are more complicated than they should be:
- Because there is no interoperability across data systems, developers must figure out how to get access to data, even if that data already exists in other places. This usually involves integration with dozens of API’s and using custom clients and protocols to access the data.
- Apps need to have a secure identity mechanism so people can log in, which today either means relying on incompatible identity solutions offered by large vendors or deploying your own.
- Custom data models, protocols, and authorization mechanisms must be devised and used in order to store and manage application data. This comes with its own unique set of challenges in the form of security and compliance with legal requirements.
In order to ease these burdens , Developers require standard interfaces for identity and authorized data access, into which multiple providers can plug in. That allows developers to no longer worry about solving secure identity and storage themselves: instead, they can rely on spec-compliant third-party services. Rather than having to integrate with specific bespoke platforms, developers can build for the standard and can responsibly reuse data from existing storage servers rather than having to set up their own.
Proposed approach
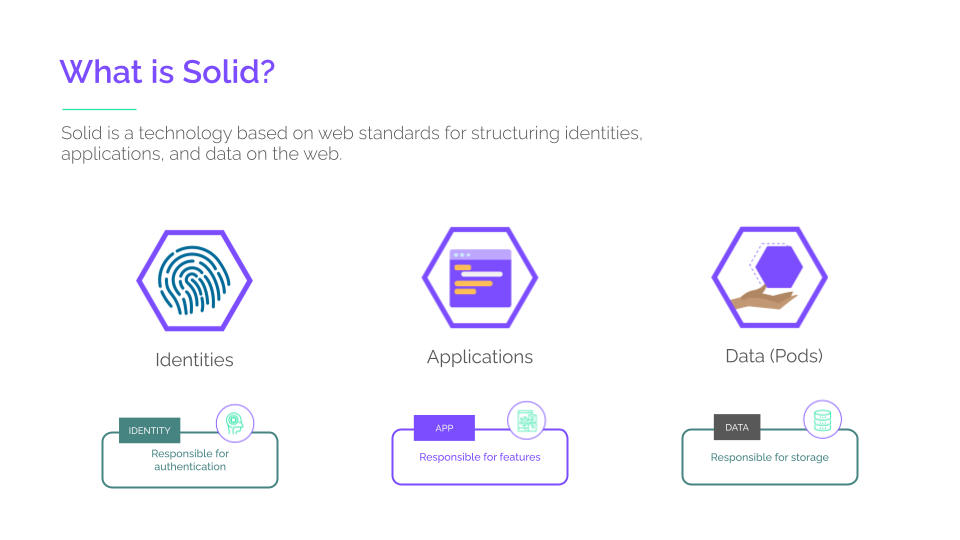
The Solid Protocol solves these problems by decoupling apps, identity, and data. In order to align on the interfaces between those 3 parties, we need standards for identity and authorized data access.
The result is that any app can work with any identity provider or any storage provider. This means that end users can manage their identity and their data, independently of the apps they want to use, and app developers don’t have to worry about storing or collecting data. Service providers can create different offerings for different kinds of use cases and end users.
The Solid Protocol is a network protocol between Clients (Applications), Servers (Data), and Identity Providers. We refer to the data a user has control of on a server as a Pod.
The Solid Protocol has the following properties which give users and developers great value:
- The app functionality is all in the client.
- Any App can work with any Pod. The user typically chooses which Pod.
- The server does not care which app is running so long as it is authenticated and authorized.
- Changes to app functionality require just the re-release of the client, and no changes to the server.
Once the Solid Protocol spec is stable, then new interoperable apps can be created by rolling out new “client-client” specs for each domain such as contacts, medical data, financial data, and so on.
Practical usage with example code
Demo apps to demonstrate the basic principles of decoupling apps, data, and identity:
- Penny
- GitHub - NoelDeMartin/umai: Offline-first Recipes Manager
- Track your movies with Media Kraken.
- List of Hello World Apps @@
Real-world deployments:
- Janeiro Digital case study: Addressing Interoperability in the NHS
Tutorials for developers:
- Building Solid Apps with LDO
- Inrupt Java Client Libraries
- React Components for Solid
- From Zero to Hero with Solid
Other venues
- The Solid Matrix rooms are generally the main day to day chat:
- Solid chat main room
- Solid app development
- Solid-specification for CG discussion of the spec
- There is a forum for longer term topics
- There is the mailing list of the Community group.
- Video recordings of Solid World webinars are here.
- The home page of the Solid Project web site should be able to take you to tutorials
Alternative approaches
The Solid Protocol is modular, in that parts of it, like in the table below, can be changed with time, typically using the Accept headers.
|
Functionality |
Previous |
Current |
Reason |
|
Authentication |
WebId-TLS |
OIDC |
Browsers opposed/ Industry norm |
|
PATCH format |
Sparql-Update |
N3 Patch |
Behavior under DELETE failure; Need more metadata |
|
Listen |
Web sockets |
Secured WS (etc) |
Security |
The Solid Protocol is also designed to be, itself, a module in a larger system, being combined with other technologies like:
- Decentralized Identifiers (DIDs) v1.0
- Verifiable Credentials Data Model v1.1
- ActivityPub
- Braid
- PROV-O: The PROV Ontology
- Consent management systems
- …
Considered accessibility, security, and privacy implications
Accessibility
The fact that the user can use multiple alternative apps means that differently abled users will be able to use apps which do the same thing in very different ways, for example conversational apps and graphics-based apps accessing the same data.
Solid Apps are web apps, and so all the knowledge and importance and techniques and guidelines which apply to Web Apps and PWAs also apply to Solid Apps.
Security
Protecting user data in the Solid system is of utmost importance. The Solid protocol requires encryption for all transmissions, ensuring safety of data during transfer. Encryption at rest and within processing also plays a pivotal role in security development. However, it's essential to emphasize that these measures are related to, yet distinct from, the network protocol. Strong authentication using keys are naturally part of the access controls to establish a foundation for trustworthy personal data storage, based on principles of confidentiality, integrity, and availability achieved within the Solid system.
The Solid protocol introduces an innovative market for pods that serves a diverse range of organizations such as commercial enterprises, nonprofit entities, and government agencies. Within this market, these organizations provide a variety of pod products, each tailored to specific needs and preferences. Notably, these products differ not only in their functionalities but also in the levels of security they offer, catering to a wide spectrum of users with varying safety requirements.
Apps like social networks, which can use Solid to store their distinct sets of sensitive data in a pod, make a very compelling case for improving online safety. While users must ensure the safety of their pod data, and will have many options and services available to do so, the Solid approach fundamentally minimizes their vulnerability to attacks on the data stores as each Pod is isolated from every other Pod. Consequently, users on pods face less risk, benefiting directly by isolation from the usual news of large-scale indiscriminate breaches. Moreover, a pod setup empowers users to easily migrate their data without losing app functionality (low or no exit barriers), taking it to a safer (more representative of their needs) environment should they deem their current provider to be compromised. Privacy value, which is increasing yet currently bottled up and depressed by steep exit barriers, will greatly expand the online app development market as safer data storage options are enabled by the Solid protocol.
Privacy
The Solid protocol upends the traditional notions of user privacy compared to the prevalent online ad-based systems of the past. Solid's architectural design prioritizes data privacy by default, marking a paradigm shift in how user information is handled.
Within a Solid pod, data is inherently private, creating a secure digital enclave where users maintain control over their information, deciding whether to share it broadly or selectively with specific groups like family or healthcare providers.
Acknowledging the pivotal role of user consent in meaningful data exchanges with services, Solid systems seamlessly integrate consent management into data-sharing flows. This involves clear and user-friendly processes for users to grant permission for the processing of specific data sets by designated entities for predefined purposes.
Solid further simplifies compliance with regulations like the General Data Protection Regulation (GDPR), streamlining the development of systems that adhere to stringent privacy standards. The introduction of the ability to understand the purpose of how data is being used underscores Solid's commitment to user-centric privacy, and also provides for when regulators are going to make AI safe. Users not only control data access but also gain clarity regarding the context and purpose of its usage, controlling processing even for knowledge systems, through transparent consent mechanisms, achieving a delicate balance between privacy and utility.
Solid offers a measured and user-oriented approach to privacy, demonstrating that effective privacy measures seamlessly coexist with and enhance digital services. It provides a perspective where privacy is an integral aspect of the user experience without the need for repetitive, tiresome and explicit summaries.
Digital Sovereignty
The ability of a user to be a first-class participant in their digital identity management, their digital sovereignty, is crucial. This need has driven a lot of investment in systems like blockchain, where everyone stores everything, or IPFS, where everyone stores a randomized fraction of other people’s data. The Solid Protocol better answers this need to re-empower people, by using and extending existing web protocols and efforts.